Once Windows Virtual Protector is installed, it creates a few malicious files on your computer and modifies Windows registry so that the threat runs automatically when Windows starts. Then it starts a fake system scan and reports false or exaggerated system security threats on your computer and locks the system completely, preventing any files from being executed. For example, if you try to run your web browser you will get a fake firewall notification saying that your web browser is infected. It blocks system tools as well, so you can just terminate its process using Task Manager or remove malicious Windows registry modifications using Registry Editor. This can't be done in Safe Mode nor Safe Mode with Networking, only in Safe Mode with Command Prompt. I you will find a step-by-step guide on how to deal with this infection below.
Windows Virtual Protector setup file has been detected by at least 6 anti-virus scanners (VirusTotal report).
When running, Windows Virtual Protector also displays fake notifications. Here's the fist one.
Error
Attempt to modify registry key entries detected. Registry entry analysis is recommend.
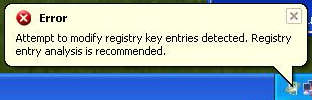
Here's another one.
Error
Potential malware detected. It is recommend to activate the protection and perform a thorough system scan to remove the malware.
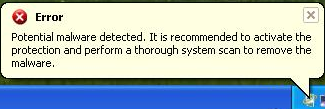
All these notifications are false, you can safely ignore them.
Windows Virtual Protector basically asks you to buy the software in order to unlock the computer and supposedly found malware. The pay for is quite simple and as you can see in the image below, a lifetime license would cost you $100. DO NOT BUY IT! If you already paid for it then please contact your credit card company as soon as you can and dispute the charges. Tell them that Windows Virtual Protector is a scam. If you are lucky enough, $100 won't be deducted from your credit card.
You have arrived at this page probably because your computer is infected with Windows Virtual Protector virus. To remove it from the system, please use the removal guide below. If you have any questions, leave a comment below. I will try to reply as soon as I can. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Windows Virtual Protector removal instructions:
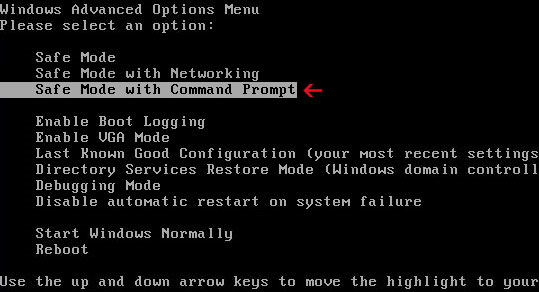
1. Reboot your computer in "Safe Mode with Command Prompt". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Command Prompt" and press Enter key.
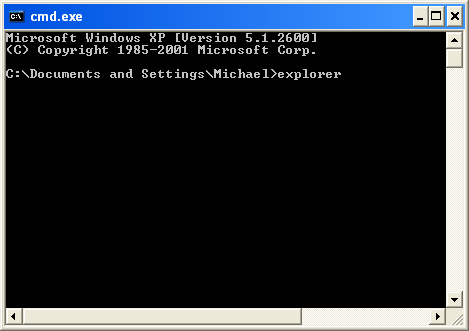
2. Login as the same user you were previously logged in with in the normal Windows mode. When done, the Windows Command Prompt will open and you will see a screen similar to the one below.
3. Once the Command Prompt appears type in explorer and hit Enter.
4. The Windows desktop will now appear. When the desktop appears you can then close the Command Prompt window by clicking on the X.
5. Write the text in bold below to Notepad.
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]
"GuardSoftware" =-
[HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon]
"Shell"="explorer.exe"
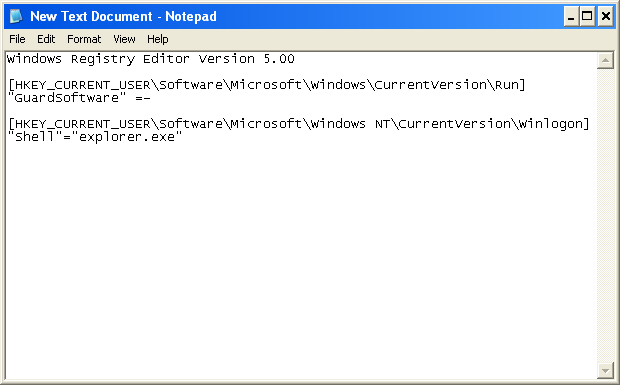
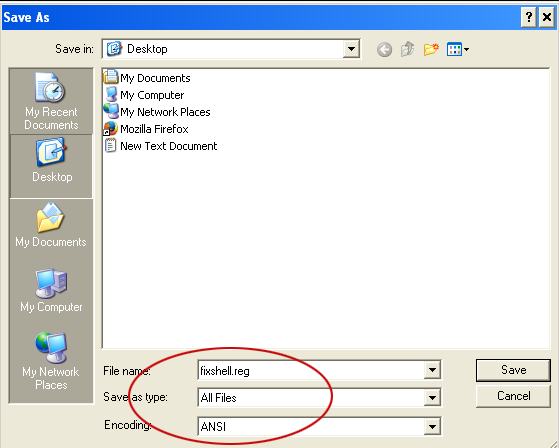
6. Save file as fixshell.reg to your Desktop. NOTE: (Save as type: All files)
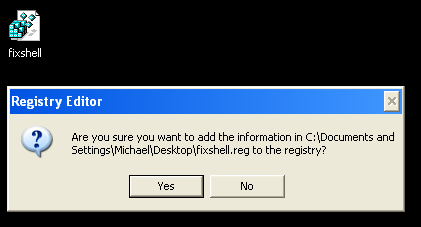
7. Double-click on fixshell.reg to run it. Click Yes for Registry Editor prompt window. Click OK.
NOTE: if you can't create the file as explained or you get an error, you can download the shellfix.reg file on a clean computer and burn it on to a CD or save it to a USB drive so that you can transfer the file to the infected computer. Then insert your CD or USB drive and double-click on the shellfix.reg and allow the data to be merged when you are prompted. Once the data has been merged, you can press the OK button and remove the removable media from your computer.
8. Please reboot your computer into the Normal Windows Mode and login as the infected user.
9. Now that you are at your normal Windows desktop, download recommended anti-malware software and run a full system scan. It will detect and remove this infection from your computer.
Associated Windows Virtual Protector Files:
- C:\Documents and Settings\[User]\Application Data\guard-[random].exe (Windows XP)
- C:\Users\[User]\AppData\Roaming\guard-[random].exe (Windows 7)
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "GuardSoftware"
- HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon "Shell"="C:\Users\[User]\AppData\Roaming\guard-[random].exe"



Không có nhận xét nào:
Đăng nhận xét