You may ask, where did this CoinVault virus come from? It's usually installed by other malware, mostly Trojan horses. You may well remember the ancient Greek myth about the giant wooden Trojan horse which was created by the Greeks in order to infiltrate the City of Troy. You may also be wondering why this article about malware is opening with such an old story. That's because the Trojan horse of yesteryear and its modern day equivalent have a lot more in common than you may think.
This type of malicious software, the Trojan Horse, did indeed take its name from the tale and once you know just how Trojan Horse malware works, it will all make perfect sense! If you still remember your history or classics lessons then you'll know that the siege of Troy lasted for many years, resulting in a stalemate which drove the Greeks to take desperate measures. After building their wooden horse they rolled it to the city gates and claimed it was a peace offering to the Trojan people. However, unbeknown to the (un)lucky recipients, the Greek army was actually hiding inside the horse and as soon as it was taken beyond the city gates and night fell, the Greek soldiers climbed out and opened the gates to their waiting army. And that, in a nutshell, is pretty much how a modern Trojan Horse works: it looks innocent but it has been specifically designed to cause a great deal of harm.
As did their ancient namesake, today's Trojans make use of their victims' susceptibility to play a role in the attack. And a lot like the horse of yore, Trojan Horses in 2014 are designed to wreak havoc on their target. CoinVault ransom Trojan will cause irreparable damage to your files, corrupt your data and can leave your computer's security in tatters. Unlike other forms of malware they do not steal data or assume your identity or try to steal money from you, they really have just been created on the whim of some spiteful software developer. The bad news is that you won't even notice when this virus will start encrypting your files unless you are constantly monitoring your CPU usage, etc. When it has finished encrypting your files it will then display a ransom screen that explains how you can pay a ransom to get your files back.
Your personal documents and files on this computer or device have just been encrypted.
Encrypted means you will not be able to access your files anymore, until they are decrypted.
Your original files have been deleted, these can be recovered as described below.
Click on "View encrypted files" to see a list files that got encrypted.
The encryption was done with a unique generated encryption key (using AES-128).
The only way to decrypt your files, is to obtain your private key and IV.
The private key, which will allow you to decrypt and get your original files back, is stored on our server. Each time the timer hits zero, the total costs will raise with the starting price.
To receive your private key, you need to pay the amount of bitcoin displayed left of this window (costs).
You need to send the amount of bitcoins to the bitcoin address at the bottom of this window.
After the purchase is made, please wait a few minutes for conformation of the bitcoins.
After the bitcoins are confirmed, click the 'check payment and receive keys' button.
Your keys will appear in the texboxes. After that, you simply click 'decrypt using keys', your files will be decrypted and restored to their original location.
Each encrypted file is stored in CoinVaultFileList.txt file. Each user will be assigned a different bitcoin address to make it harder to monitor payments for CoinVault. Other ransom Trojans use TOR or similar web services to collect the payments. This virus acts as the decrypter and payment system thus eliminating any other services that could be used by authorities to track cyber crooks down. So, as I said, even though it's not the most sophisticated ransomware I've ever seen it's still a very dangerous infection.
When running CoinVault will block pretty much every executable file in order to protect itself from being removed. It means it will probably block your antivirus program as well. If you can't run any malware removal tool on your computer then restart the system in Safe Mode or Safe Mode with Networking and try again. What is more, this virus will change your Windows wallpaper saying "Your files have been encrypted!".
Some Trojans Horses are associated with instant messenger apps – now such a popular way of keeping in touch – as well as file sharing tools, however they are mostly spread via spam email. And it is that is where the scammers need to get creative (just like those ancient Greeks) by convincing you to open an attachment or link in an email or instant message. Once you've done that, you will be attacked from within your own city wall, as it were.
How can I defend myself from attack by CoinVault? Fortunately there are a few things you can do to protect yourself from the chaos caused by this ransom virus. Make sure that you have a good anti-malware program installed on your PC or laptop and keep it up to date, and scan your machine with it manually on a regular basis. Keeping Windows updated too is crucial as this will ensure that you have the latest versions of security patches. Finally, you know it, but are you still guilty of it? Don't download unknown programs and never open emails or attachments from senders you don't recognize. And last, but not least, backup your files! Having backups in place will save you headaches and time, trust me. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing CoinVault and related malware:
Before restoring your files from shadow copies, make sure CoinVault is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by CoinVault virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Before using Shadow Explorer, you can try to decrypt some of your files using RakhniDecryptor.exe and RectorDecryptor.exe from Kaspersky. These tools might help you, but please note that they were not designed decrypt the data encrypted by this ransomware virus. However, you can still try them.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
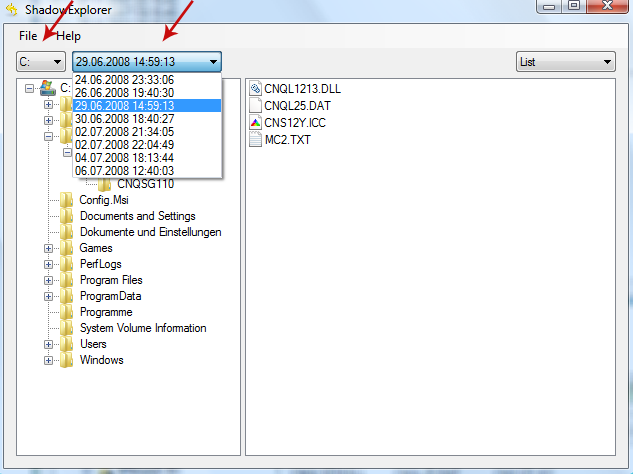
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
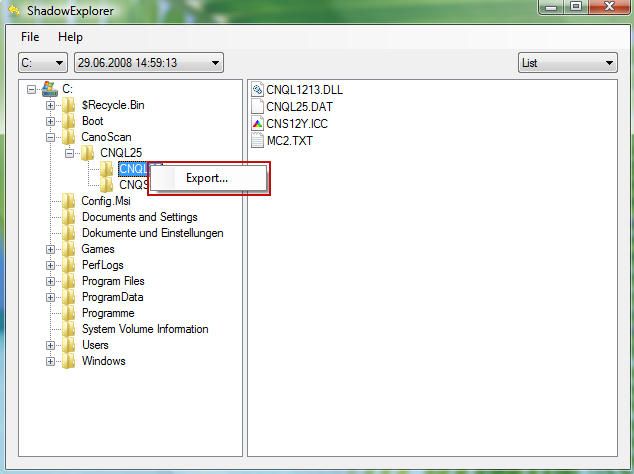
Hopefully, this will help you to restore all encrypted files or at least some of them.



Không có nhận xét nào:
Đăng nhận xét