Attention! Your computer was attacked by virus-encoder.
All your files are encrypted cryptographically strong, without the original key recovery is impossible!
To get the decoder and the original key, you need to to write us at the email decode@india.com with the subject "encryption" stating your id.
Write in the case, do not waste your and our time on empty threats.
Responses to letters only appropriate people are not adequate ignore.
As you can see, cyber crooks will only respond to properly written emails with your ID. I wouldn't recommend paying the ransom but if the data encrypted is very important to you, I mean so important that you can't afford to lose it then you may consider sending them 1 bitcoin. But remember, there's really no guarantee that they will send you the decoder and the key. So, you may lose your money and not just your files. Think twice before paying the ransom and don't supper scammers.
Another important question is how did you get this virus? For today's Trojan Horse has more than a name in common with its olde worlde counterpart; in other words, the giant wooden horse that the Greek army built and offered to the people of Troy as a peace offering during the two nation's lengthy war. You see, the Greeks built this horse in order to ambush the Trojans and hid their men in its hollow stomach. Once the Trojans had accepted the, albeit rather strange gift (maybe it made sense at the time!) and wheeled it into the city, the soldiers crept out after nightfall and opened the city gates to their fellow countrymen. In this way, the City of Troy was taken and the Greeks won the war. Yes, it was a sneaky tactic, but as they say, all's fair in love and war. Ok, you may think that this story is unrelated but it actually isn't. So what does this have to do with our modern day Trojan? Well, just as the Greek army used their rather deceptive method to infiltrate Troy and attack it from within, so too will Trojan Horse malware infiltrate your PC and cause you harm from inside your own machine. This decode@india.com file encryption Trojan is distributed in various sneaky ways as well. Most of the time, it is downloaded from scam emails with invoices from well know companies and online shops. Be very careful opening attachments like inviuce_2014_11_854125478.zip because you may easily infect your computer with this ransom Trojan.
What do ransom Trojans do?
Trojan malware is a program which purports to be harmless – or even offer useful benefits - but the reality is very different and it can, and will, cause chaos to your files and data.
On the plus side, Trojan Horse malware is usually easy to spot, once it's been installed, that is. These are some of the telltale signs which will help you recognize a Trojan:
- Your PC is sluggish and programs keep crashing
- You're online but it's taking ages to open websites
- Your PC or laptop take much longer to start up when you try and log in
- There is something you don't remember downloading in your list of installed programs
- There are icons that you have never seen before on your desktop
- You have a new tool bar that you've never seen before
- Your default settings have changed and refuse to return to normal
- You're seeing a large number of pop up or pop under adverts
- And for the ransom Trojan one sign is more than obvious: all your files are encrypted and you can't open tehm
The good news is there are things you can do to defend yourself from Trojans:
- Install a reputable anti-malware program on your computer and ensure it's the latest version and your patches are up to date
- Use a firewall to block unwanted connections
- Be discerning about the type of websites that are visited on your computer. Adult and gambling (to name two) are prime Trojan Horse stomping grounds
- Don't open attachments or click on links in emails if you don't know the sender
- And most importantly, create backups. Every week or month or every time you need. Having backups will help you a lot in case your computer gets infected with a ransomware virus like this one
If you have any questions, please leave a comment below. Last, but not least, if there's anything you think I should add or correct, please let me know. It might be a pain but the issue needs to be dealt with – and the way to do it is by not giving in, not paying up and not letting the attackers win.
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing decode@india.com ransomware and related malware:
Before restoring your files from shadow copies, make sure this ransom Trojan is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by this virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Before using Shadow Explorer, you can try to decrypt some of your files using RakhniDecryptor.exe and RectorDecryptor.exe from Kaspersky. These tools might help you, but please note that they were not designed decrypt the data encrypted by this ransomware virus. However, you can still try them.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
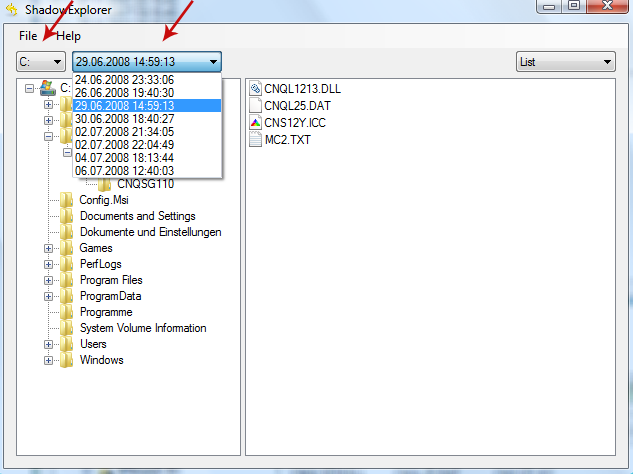
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
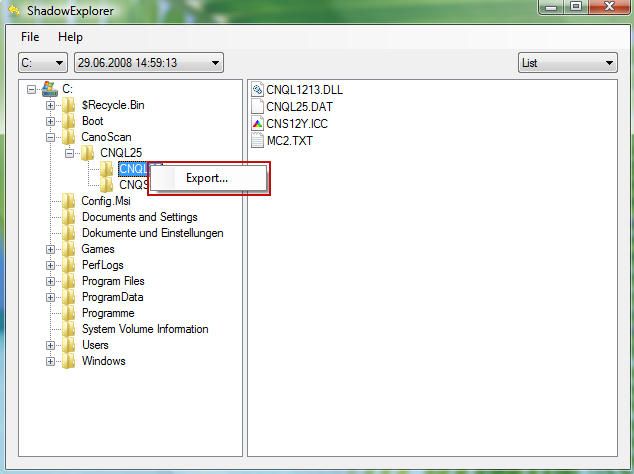
Hopefully, this will help you to restore all encrypted files or at least some of them.


Không có nhận xét nào:
Đăng nhận xét