Do you remember the ancient Greek myth about the Trojan horse? The gigantic wooden horse that members of the Greek army hid inside to trick their enemies in Troy into giving them access to the walled city they held under siege – consequently attacking them in the dead of night after opening the city gates to their fellow soldiers. Are you wondering where I'm going with this? Well, knowing the background of this story, gives you a very good idea of what a modern day ransomware is all about.
Today's Trojan Horses are a form of malicious software, more commonly referred to as malware. And just as the Greek army conned their way into the city of Troy by making the inhabitants believe the wooden horse was a peace offering, this CryptoWall malware sneaks its way onto your PC by also asking you to invite it in. What is more, the latest variant of this malware is very sophisticated. It uses unique bitcoin payment addresses to track every infected computer. Cyber crooks have their own TOR gateways operating under the following domains: tor4pay.com, pay2tor.com, tor2pay.com, and pay4tor.com. Some of these domains may be blocked but or changed any time but the fact is that scammers will not run short of Web-to-TOR gateways any time soon. The unique URL where you need to go using TOR browser looks like this: paytorhrosnsbfkd.tor4pay.com. The first part is your unique number then goes the web to TOR gateway. CryptoWall creators have also improved the way files are encrypted and deleted from the computer minimizing recovery chances close to zero if you don't create back ups. However, there are still some tricks that can help you restore at least some of your files. For more details, please follow the steps in the removal guide below.
Here's how the DECRYPT_INSTRUCTION.HTML reads:
What happened to your files ?
All of your files were protected by a strong encryption with RSA-2048 using CryptoWall 2.0.
More information about the encryption keys using RSA-2048 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
What does this mean ?
This means that the structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them, it is the same thing as losing them forever, but with our help, you can restore them.
How did this happen ?
Especially for you, on our server was generated the secret key pair RSA-2048 - public and private.
All your files were encrypted with the public key, which has been transferred to your computer via the Internet.
Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do ?
Alas, if you do not take the necessary measures for the specified time then the conditions for obtaining the private key will be changed.
If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist.
Ok, so how it does this is by disguising itself as a program which has the appearance of something useful – and harmless. Perhaps it will look like a game, or maybe even an anti-virus program! Whatever guise it takes, you probably won't think that it could be designed to do you harm. Just like you don't think that an email from UPS may contain malware. You may be alerted to the existence of the malware by a pop up window or in an email sent by the software developer behind the malware. In all innocence you click on the pop up or email link or attachment and this will trigger the CryptoWall malware, allowing it to gain access to your operating system.
It can also be hidden in ActiveX controls on targeted websites or hidden in freeware and shareware. Not to mention infected websites that redirect users to exploit kits. Nowhere is safe!
Once the malware is installed on your computer it may be also working behind the scenes to gather your personal data – such malware can log your keystrokes so they know what you're entering or typing and they can also steal data from your hard drive. They can also divert data before it's reached the server it was intended for. The problem is that you can't really know how badly your computer was infected. Before recovering your files it's very important to remove all malware from your computer.
As you probably already know, some Trojan Horses are created simply to wreak havoc on your machine, deleting files and modifying your operating system. Others will add fuel to the fire by downloading even more malware. CryptoWall is some where between. However, regardless of whether a hacker is utilizing a Trojan to cause trouble for their own entertainment or to steal your identity you really need to be defending yourself.
So how do you do that exactly? Such malicious programs often use the .exe file extension in Windows so you should not run these unless you are certain that you know and trust the source. It goes without saying too, that you should ensure your anti-malware program is by a reputable company and that you run it frequently and keep it bang up to date.
One other tip is to shut your computer down properly and not leave it in sleep mode when it's not in use. Malicious programs, mostly Trojans, scan networks and the Internet looking for vulnerable operating systems and therefore by default, the longer you leave your PC switched on, the more chance you have of being found by a Trojan.
So how do you protect yourself and avoid being attacked again by CryptoWall? That's the 60 million dollar question, surely? To protect yourself you really need to know how it infects your computer in the first place. And we have to break it to you; you installed yourself!
That's because Trojans are designed to look innocent and will dupe you into opening – and running – them on your PC. To limit the chances of this happening again in future there are a number of things that you should (and shouldn't) do. Here's are a couple of the most important things to remember.
- Never open emails from senders that you don't know - and if you do so by accident, definitely do not download any attachments or click on any links in that email. If spam makes its way into your inbox, delete it.
- Ensure you have a reputable anti-malware program running on your PC. It must be up to date too so make sure you upgrade it with any new versions or patches released by the developer.
- Also be careful when you look at (or avoid visiting!) websites of an adult or dubious nature as these may have been infected by CryptoWall.
- Also, consider enabling software restriction policies, some useful info can be found here.
We hope this helps you stay safe and avoid the menace of this malware.
Of course, the most frequently asked question is how to restore files encrypted by CryptoWall? The best method is obviously to restore your files from a recent backup. If you have been performing backups, then you should use your backups to restore your files. If you don't have backups then you can try restoring your files with a program called Shadow Explorer. It may work and or may not. I know some users managed to get at least some of their files back using this program. You can try it too. There's really nothing to lose after all.
Another question I often get is about the decrypt program. Does it really work or maybe it doesn't even exist? Well, that's a good question because cyber crooks can surely lie about it. However, a few readers have confirmed that after sending bitcoins to cyber crooks they got a download link for decrypter.zip. The download usually includes the decryptor program and 2 files with keys. They ran the program. Decrypting started and finished successfully. Don't get me wrong, I don't recommend paying the ransom and supporting their evil business. However, I know that some people can not afford losing important data. Since there are no working decryption tools right now, some people are simply left without a choice.
If you have any questions, please leave a comment down below. Last, but not least, if there's anything you think I should add or correct, please let me know. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing CryptoWall and related malware:
Before restoring your files from shadow copies, make sure CryptoWall is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by CryptoWall malware:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Before using Shadow Explorer, you can try to decrypt some of your files using RakhniDecryptor.exe and RectorDecryptor.exe from Kaspersky. These tools might help you, but please note that they were not designed decrypt the data encrypted by this ransomware virus. However, you can still try them.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
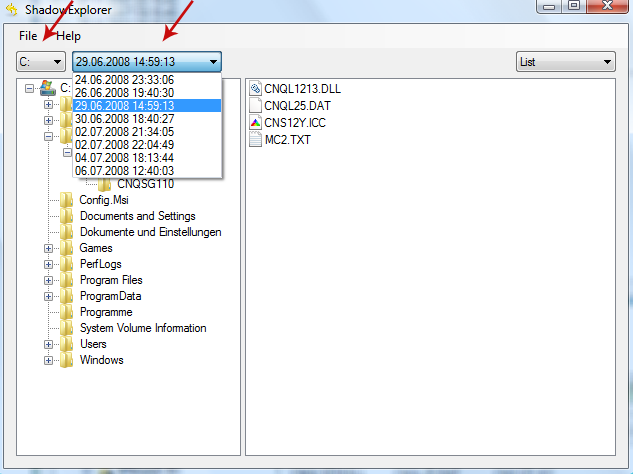
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
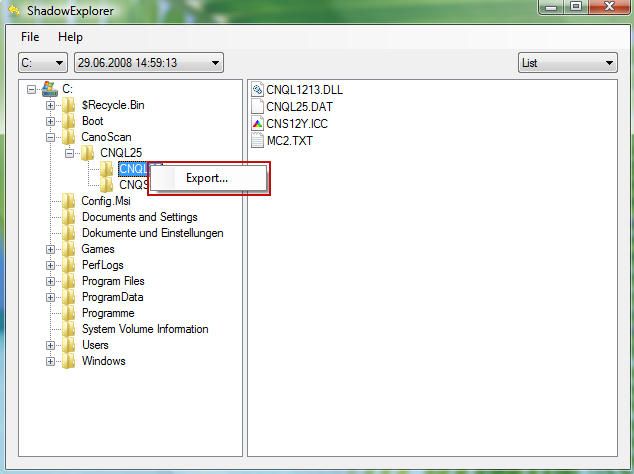
Hopefully, this will help you to restore all encrypted files or at least some of them.


I have bookmarked your blog, the articles are way better than other similar blogs.. thanks for a great blog! cpa network
Trả lờiXóa