So, as I said, the rogue program will change Windows Shell value from explorer.exe to its own executable file which typically can be found in the Application Data folder. As a result, you won't see any files on your Desktop and you won't be able to use Task Manager, MSConfing and other useful Windows tools in Normal Mode. It will also change the Image File Execution Options registry keys.
How does rogue security software get on my computer? I would say mostly through drive-by downloads which exploit security vulnerabilities and infected websites. Windows Premium Shield is also promoted via fake security scanners, peer to peer networks and malicious email attachments. Most of the time, user’s interaction is not required. Simply visiting an infected website is enough to infect your computer. What is more, scareware can be download dropped directly to infected computer if they belong to a certain botnet.
When running, Windows Premium Shield will display fake security alerts claiming that your web browser is infected or that your system data security is at risk. It may also display bogus security alerts about Trojan activity and identity theft attempts. Just like the fake scan results, these security warnings are fake and can be ignored.
Windows Premium Shield belongs to the FakeVimes fraudware family.
Most importantly, do not purchase this bogus anti-virus program. Do not follow the on screen instructions and do not purchase it "to protect your system." If you have purchased it, please contact your credit card company and dispute the charges stating that the program is a scam and a computer virus. To remove Windows Premium Shield and other related malware, please use the removal guide below. If you have any questions, please leave a comment below.
Written by Michael Kaur, http://deletemalware.blogspot.com
Windows Premium Shield removal instructions:
1. Reboot your computer in "Safe Mode with Command Prompt". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Command Prompt" and press Enter key.
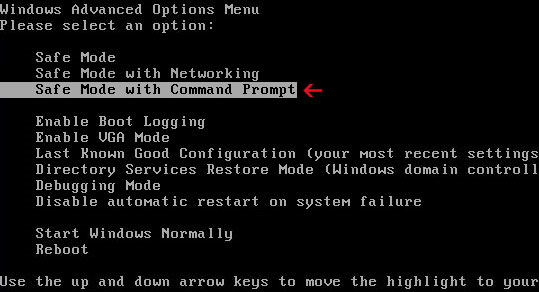
2. Login as the same user you were previously logged in with in the normal Windows mode. When done, the Windows Command Prompt will open and you will see a screen similar to the one below.
3. Once the Command Prompt appears type in explorer and hit Enter.
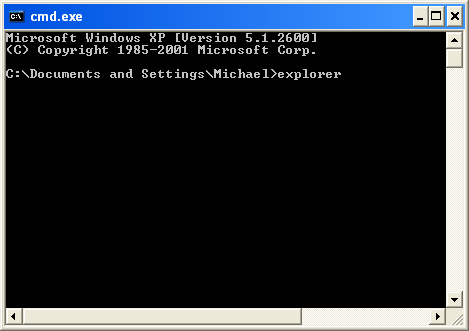
4. The Windows desktop will now appear. When the desktop appears you can then close the Command Prompt window by clicking on the X.
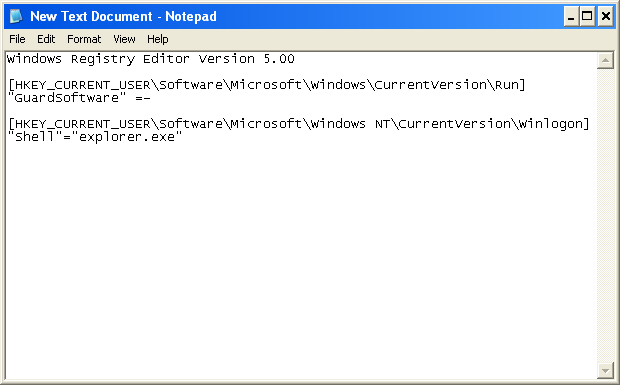
5. Write the text in bold below to Notepad.
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]
"GuardSoftware" =-
[HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon]
"Shell"="explorer.exe"
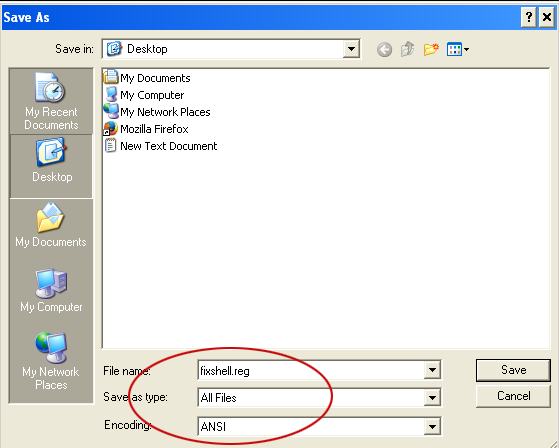
6. Save file as fixshell.reg to your Desktop. NOTE: (Save as type: All files)
7. Double-click on fixshell.reg to run it. Click Yes for Registry Editor prompt window. Click OK.
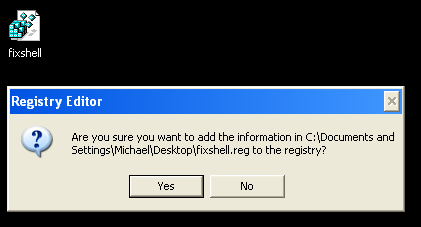
NOTE: if you can't create the file as explained or you get an error, you can download the shellfix.reg file on a clean computer and burn it on to a CD or save it to a USB drive so that you can transfer the file to the infected computer. Then insert your CD or USB drive and double-click on the shellfix.reg and allow the data to be merged when you are prompted. Once the data has been merged, you can press the OK button and remove the removable media from your computer.
8. Please reboot your computer into the Normal Windows Mode and login as the infected user.
9. Now that you are at your normal Windows desktop, download recommended anti-malware software and run a full system scan. It will detect and remove this infection from your computer.
Associated Windows Premium Shield Files:
- C:\Documents and Settings\[User]\Application Data\guard-[random].exe (Windows XP)
- C:\Users\[User]\AppData\Roaming\guard-[random].exe (Windows 7)
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "GuardSoftware"
- HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon "Shell"="C:\Users\[User]\AppData\Roaming\guard-[random].exe"


Không có nhận xét nào:
Đăng nhận xét