If you already paid for it, please contact your credit card company and dispute the charges. In reality you've just paid for something which has been designed to look like anti-virus software by pretending to scan your laptop or desktop and fake the removal of viruses which weren't there in the first place! The other worrying thing is that you've also just handed over your bank details to someone who profits from making money fraudulently online.
Put simply Windows Protection Booster can be a real pain when you're using your computer. But how does it get on your computer in the first place? Let's take a closer look.
It can be installed when you visit a site that has been infected, or you've downloaded something which has been bundled with it. Other rogue anti-viruses are drive-by downloads. These download and install themselves without any action from you at all. In the majority of cases they do so by exploiting vulnerabilities in your browser, Java and Adobe programs. So, make sure these are updated all the time.
And if you think that you're probably safe from being targeted by Windows Protection Booster because you don't visit 'the sorts of websites' that would likely be infected and you don't do much downloading, think again. Do you use Facebook? Chances are, like many of us, you do. Well here's the thing because not only can browsing the Internet be dangerous but using social networking sites can be too. Be very careful when clicking on shady links even if they were posted by people you know and trust. Social networks are very often used to distributed rogue anti-virus programs and other malware. To learn more, please read Facebook security and privacy best practices.
Social networks have found themselves on the receiving end of a lot of unwanted attention from the creators of rogue anti-virus software and is a major target for many third-party rogue applications. These are designed to subtract your account information from you, by using deceptive tactics. For the most part these look like an added feature which attempts to lure you in by promising that you'll be able to see who views your profile for example. You're desperate to know who's stalking you so you install the app. But what you're really doing is giving the app access to your account and contacts – and it will invite your friends to download it too. So, not only could you have just installed Windows Protection Booster on your PC but your friends could be about to too!
Written by Michael Kaur, http://deletemalware.blogspot.com
Method 1: Windows Protection Booster removal using activation key:
1. Open Windows Protection Booster scanner window. Click the "question mark button" (top right hand corner of the scanner window) and select "Register".
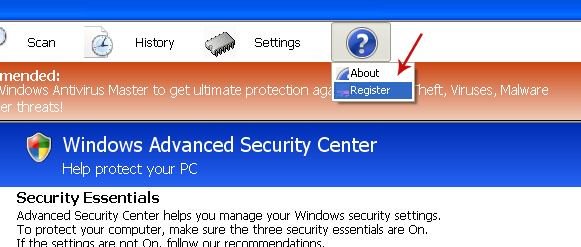
You should now see the registration form.
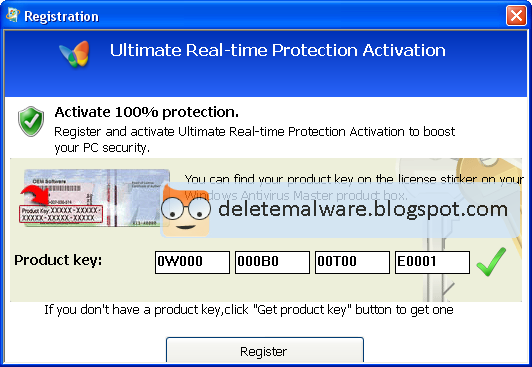
Enter one of the registration keys given below and click Register to activate this rogue security program. Don't worry, this is completely legal since it's not genuine software.
0W000-000B0-00T00-E0001
0W000-000B0-00T00-E0021 ← (new key)
0W000-000B0-00T00-E0002
0W000-000B0-00T00-E0003
Once this is done, you are free to install recommended anti-malware software and remove this malware from your computer.
2. Download recommended anti-malware software and run a full system scan to completely remove this rogue program and related malware from your computer.
Method 2: Windows Protection Booster removal instructions (Safe Mode with Command Prompt):
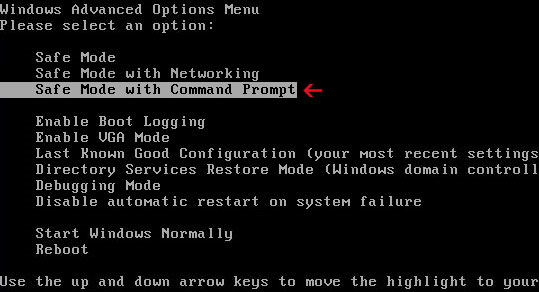
1. Reboot your computer in "Safe Mode with Command Prompt". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Command Prompt" and press Enter key.
2. Login as the same user you were previously logged in with in the normal Windows mode. When done, the Windows Command Prompt will open and you will see a screen similar to the one below.
3. Once the Command Prompt appears type in explorer and hit Enter.
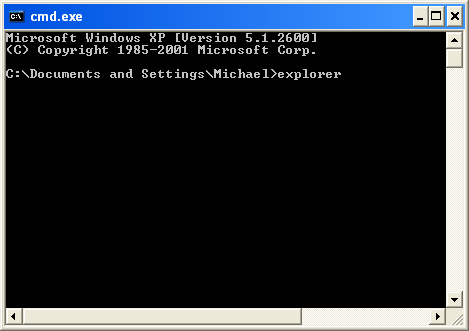
4. The Windows desktop will now appear. When the desktop appears you can then close the Command Prompt window by clicking on the X.
5. Write the text in bold below to Notepad.
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]
"GuardSoftware" =-
[HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon]
"Shell"="explorer.exe"
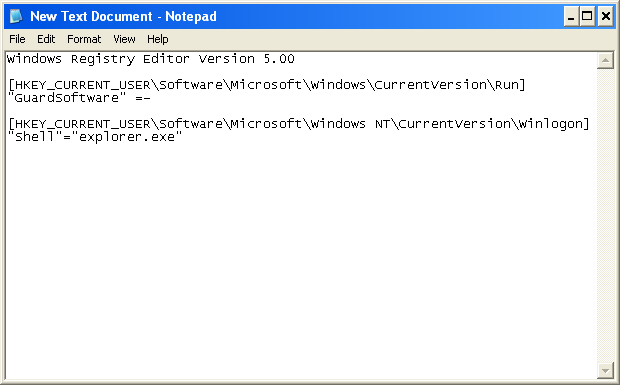
6. Save file as fixshell.reg to your Desktop. NOTE: (Save as type: All files)
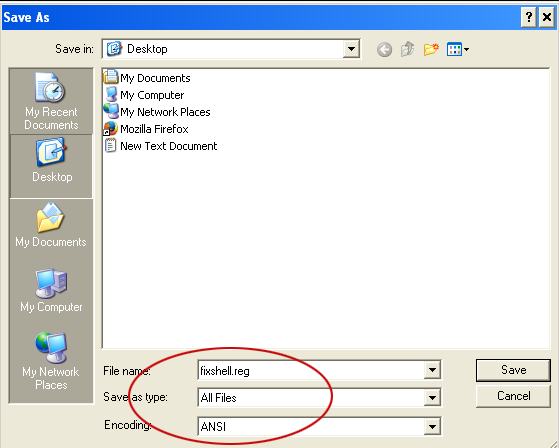
7. Double-click on fixshell.reg to run it. Click Yes for Registry Editor prompt window. Click OK.
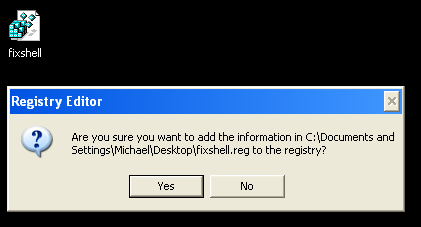
NOTE: if you can't create the file as explained or you get an error, you can download the shellfix.reg file on a clean computer and burn it on to a CD or save it to a USB drive so that you can transfer the file to the infected computer. Then insert your CD or USB drive and double-click on the shellfix.reg and allow the data to be merged when you are prompted. Once the data has been merged, you can press the OK button and remove the removable media from your computer.
8. Please reboot your computer into the Normal Windows Mode and login as the infected user.
9. Now that you are at your normal Windows desktop, download recommended anti-malware software and run a full system scan. It will detect and remove this infection from your computer.
Method 3: Windows Protection Booster removal instructions (System Restore):
1. Reboot your computer in "Safe Mode with Command Prompt". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Command Prompt" and press Enter key.

2. Login as the same user you were previously logged in with in the normal Windows mode. When done, the Windows Command Prompt will open and you will see a screen similar to the one below.
3. Once the Command Prompt appears type in explorer and hit Enter.

4. The Windows desktop will now appear. When the desktop appears you can then close the Command Prompt window by clicking on the X.
5. Once in there, go to Start menu and search for "system restore". Or you can browse into the Windows Restore folder and run System Restore utility from there:
Win XP: C:\windows\system32\restore\rstrui.exe double-click or press Enter
Win Vista/7/8: C:\windows\system32\rstrui.exe double-click or press Enter
6. Select Restore to an earlier time or Restore system files... and continue until you get into the System Restore utility.
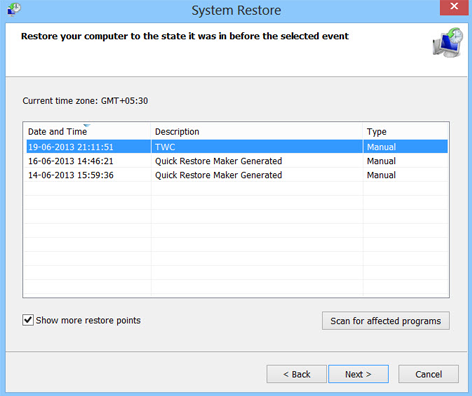
7. Select a restore point from well before the Windows Protection Booster appeared, two weeks should be enough.
8. Restore it. Please note, it can take a long time, so be patient.
9. Once restored, restart your computer and hopefully this time you will be able to login (Start Windows normally).
10. At this point, download recommended anti-malware software and run a full system scan to remove this malware from your computer.
Associated Windows Protection Booster Files:
- C:\Documents and Settings\[User]\Application Data\guard-[random].exe (Windows XP)
- C:\Users\[User]\AppData\Roaming\guard-[random].exe (Windows 7/8)
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "GuardSoftware"
- HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon "Shell"="C:\Users\[User]\AppData\Roaming\guard-[random].exe"


Không có nhận xét nào:
Đăng nhận xét